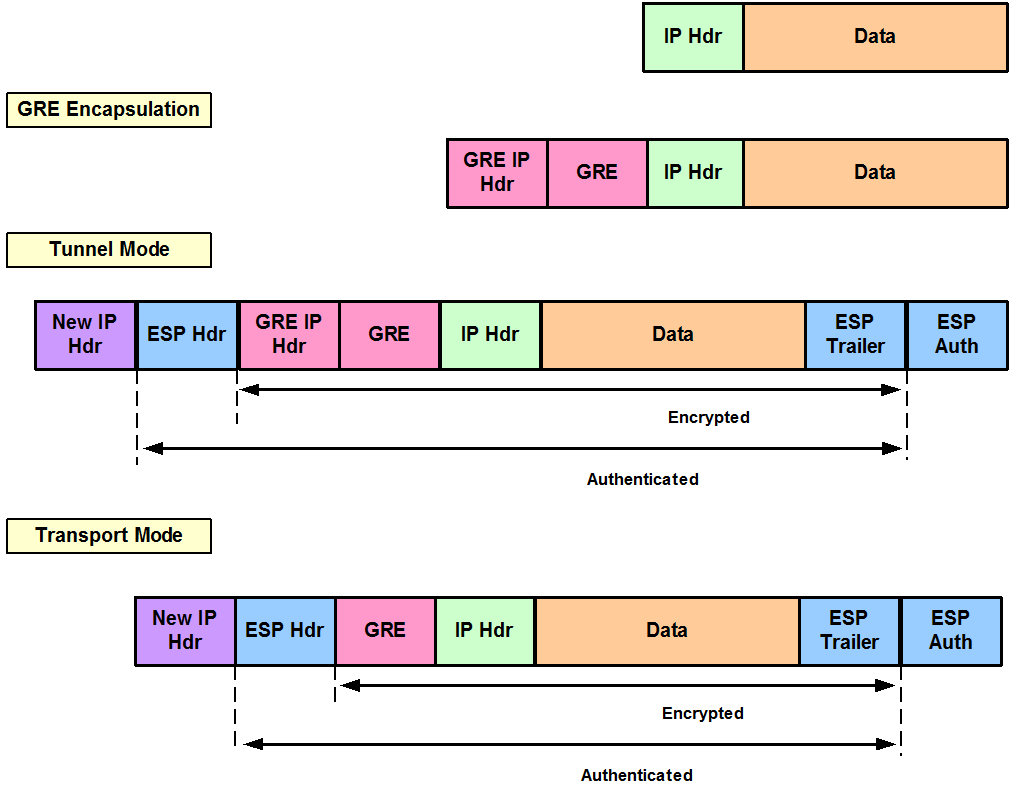
This post describes the configuration of IPsec using four different methods in order to achieve authentication and encryption. We will compare the configuration requirements as well as the overhead introduced by each method from the point of view of packet size.
(more…)Posts archive for November, 2017
Recent Comments