Azure virtual WAN (vWAN ) is undoubtedly a strong choice in the wide-area network (WAN) connectivity model, utilizing third-party backbones. It holds significant potential and functionalities, but it is also a relatively immature and evolving service with certain limitations in use cases that deviate from the Azure reference architecture.
In this post, I would like to share my first-hand experiences and lessons learned from integrating vWAN into my use case. I hope that these insights can assist you in making decisions and implementing workarounds to address challenges arising from certain limitations.
Here we go!🚀
(more…)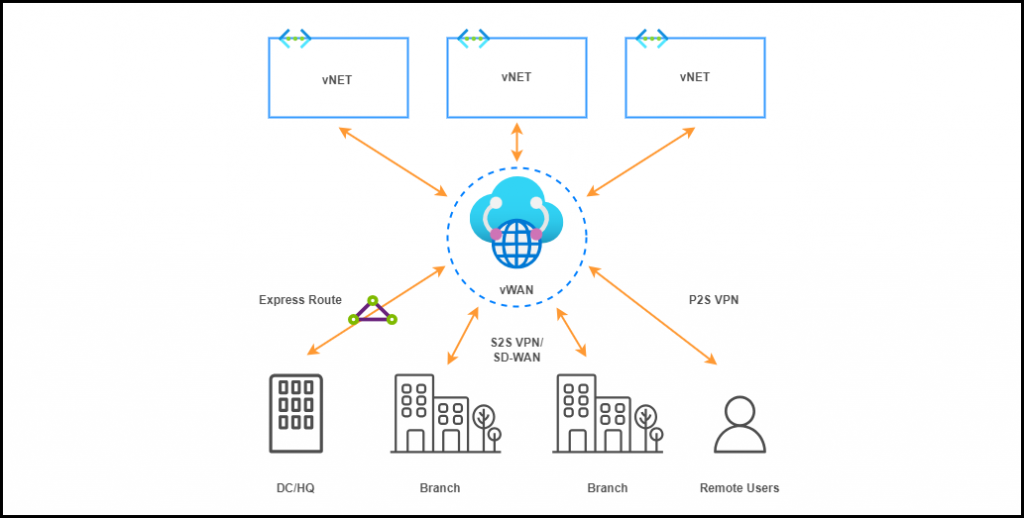
Recent Comments