IPsec: Crypto Maps, GRE and VTI
This post describes the configuration of IPsec using four different methods in order to achieve authentication and encryption. We will compare the configuration requirements as well as the overhead introduced by each method from the point of view of packet size.
Contents
- Topology
- Description
- Crypto Maps
- GRE over IPsec with Crypto Maps
- Fragmentation
- GRE over IPsec with IPsec Profile
- Fragmentation
- Virtual Tunnel Interface (VTI)
- Fragmentation
- Configuration Summary
Topology
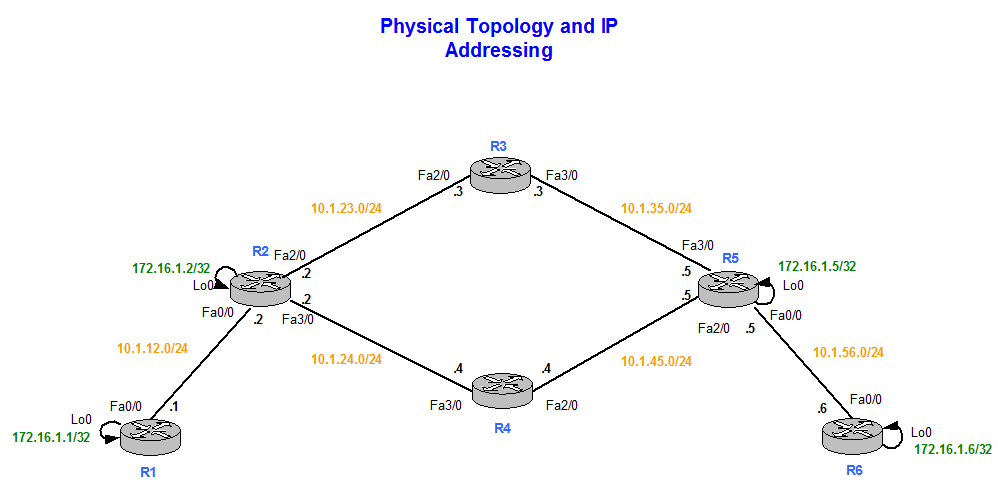
Figure 1
Description
Internet Protocol Security (IPsec) is a standard based security framework that offers authentication, integrity, confidentiality and anti-replay features. IPsec is a point to point unicast tunnel which might be a limitation to scale as a full mesh on large network deployments.
This post describes the configuration of IPsec using four different methods in order to achieve the same final goal: authenticate and encrypt packets sent between R1 and R6’s Loopback0. We will use IPsec Encapsulating Security Payload (ESP) which offers Encryption and Authentication versus IPsec Authentication Header (AH) which only offers Authentication capabilities.
These are the configuration methods we are going to discuss:
- Crypto Maps.
- Generic Routing Encapsulation (GRE) over IPsec with Crypto Maps.
- GRE over IPsec with IPsec Profile.
- Virtual Tunnel Interface (VTI) with IPsec Profile.
We will also compare the configuration requirements as well as the overhead introduced by each method from the point of view of packet size.
Notice that the intention of this post is not to explain Security Association (SA) negotiation, differences between IPsec Phase 1 (ISAKMP/IKE SA) and IPsec Phase 2 (IPsec SA) or crypto policy parameters.
Crypto Maps
Crypto Maps are used to form on demand IPsec tunnels based on interesting traffic. They do not support dynamic routing through the encrypted tunnel because they do not have an interface on the Routing Table. An extra encapsulation such as GRE (GRE over IPsec) would be needed in order to be able to enable Routing Protocols on the Tunnel interface.

Figure 2
Proxy ACL (IPSEC_TRAFFIC) defines the interesting traffic we want to protect and triggers the tunnel establishment. Proxy ACLs are configured on the end points of the tunnel and must be mirror images of each other. With Crypto Maps, Proxy ACLs can be very granular to define exactly what traffic we want to encrypt. Traffic that does not match any entry of the ACL will be routed as normal. Crypto Maps are always configured outbound by default.
Because the tunnel endpoints, R2 and R5, have two links for routing between each other it makes more sense to establish the tunnel between their loopbacks in order to reroute around a failure.
R2:
permit ip host 172.16.1.1 host 172.16.1.6
crypto isakmp policy 10
hash md5
authentication pre-share
group 14
crypto isakmp key CRYPTO_PASSWORD address 172.16.1.5
crypto ipsec transform-set ESP-3DES-MD5-HMAC esp-3des esp-md5-hmac
mode tunnel
crypto map CRYPTO_MAP local-address Loopback0
crypto map CRYPTO_MAP 10 ipsec-isakmp
set peer 172.16.1.5
set transform-set ESP-3DES-MD5-HMAC
match address IPSEC_TRAFFIC
interface FastEthernet2/0
ip address 10.1.23.2 255.255.255.0
crypto map CRYPTO_MAP
interface FastEthernet3/0
ip address 10.1.24.2 255.255.255.0
crypto map CRYPTO_MAP
R5:
permit ip host 172.16.1.6 host 172.16.1.1
crypto isakmp policy 10
hash md5
authentication pre-share
group 14
crypto isakmp key CRYPTO_PASSWORD address 172.16.1.2
crypto ipsec transform-set ESP-3DES-MD5-HMAC esp-3des esp-md5-hmac
mode tunnel
crypto map CRYPTO_MAP local-address Loopback0
crypto map CRYPTO_MAP 10 ipsec-isakmp
set peer 172.16.1.2
set transform-set ESP-3DES-MD5-HMAC
match address IPSEC_TRAFFIC
interface FastEthernet2/0
ip address 10.1.45.5 255.255.255.0
crypto map CRYPTO_MAP
interface FastEthernet3/0
ip address 10.1.35.5 255.255.255.0
crypto map CRYPTO_MAP
In order to trigger the tunnel we need to generate some interesting traffic that matches the Proxy ACL. The ping from R1’s Lo0 to R6’s Lo0 makes the tunnel negotiation process and establishment to start between the tunnel endpoints (R2 and R5). The output shows some packets have been lost but this is the normal behavior until the tunnel is finally established.
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.6, timeout is 2 seconds:
Packet sent with a source address of 172.16.1.1
..!!!
Success rate is 60 percent (3/5), round-trip min/avg/max = 44/56/72 ms
QM_IDLE state is the correct output for ISAKMP SA. This means IPsec Phase 1 was successfully completed.
IPv4 Crypto ISAKMP SA
dst src state conn-id status
172.16.1.5 172.16.1.2 QM_IDLE 1001 ACTIVE
Then we check IPsec Phase 2. The output shows that packets are being encapsulated/decapsulated and encrypted/decrypted. This is the correct output. In addition we can see that there are two SAs per interface (FastEthernet2/0 and FastEthernet3/0), one inbound and one outbound: one from R2 to R5 and one from R5 to R2. They are identified by the spis 0x90042D99(2416192921)and 0x2BA4CAE8(732220136)respectively.
interface: FastEthernet2/0
Crypto map tag: CRYPTO_MAP, local addr 172.16.1.2
protected vrf: (none)
local ident (addr/mask/prot/port): (172.16.1.1/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (172.16.1.6/255.255.255.255/0/0)
current_peer 172.16.1.5 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 3, #pkts encrypt: 3, #pkts digest: 3
#pkts decaps: 3, #pkts decrypt: 3, #pkts verify: 3
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 172.16.1.2, remote crypto endpt.: 172.16.1.5
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet2/0
current outbound spi: 0x90042D99(2416192921)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x2BA4CAE8(732220136)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: 1, sibling_flags 80004040, crypto map: CRYPTO_MAP
sa timing: remaining key lifetime (k/sec): (4349696/3523)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x90042D99(2416192921)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: 2, sibling_flags 80004040, crypto map: CRYPTO_MAP
sa timing: remaining key lifetime (k/sec): (4349696/3523)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
interface: FastEthernet3/0
Crypto map tag: CRYPTO_MAP, local addr 172.16.1.2
protected vrf: (none)
local ident (addr/mask/prot/port): (172.16.1.1/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (172.16.1.6/255.255.255.255/0/0)
current_peer 172.16.1.5 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 3, #pkts encrypt: 3, #pkts digest: 3
#pkts decaps: 3, #pkts decrypt: 3, #pkts verify: 3
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 172.16.1.2, remote crypto endpt.: 172.16.1.5
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet2/0
current outbound spi: 0x90042D99(2416192921)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x2BA4CAE8(732220136)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: 1, sibling_flags 80004040, crypto map: CRYPTO_MAP
sa timing: remaining key lifetime (k/sec): (4349696/3523)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x90042D99(2416192921)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: 2, sibling_flags 80004040, crypto map: CRYPTO_MAP
sa timing: remaining key lifetime (k/sec): (4349696/3523)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
R5 shows the same output with mirror Proxy ACL (local ident and remote ident) and spi inboud/outbound values.
IPv4 Crypto ISAKMP SA
dst src state conn-id status
172.16.1.5 172.16.1.2 QM_IDLE 1001 ACTIVE
R5#show crypto ipsec sa
interface: FastEthernet2/0
Crypto map tag: CRYPTO_MAP, local addr 172.16.1.5
protected vrf: (none)
local ident (addr/mask/prot/port): (172.16.1.6/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (172.16.1.1/255.255.255.255/0/0)
current_peer 172.16.1.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 3, #pkts encrypt: 3, #pkts digest: 3
#pkts decaps: 3, #pkts decrypt: 3, #pkts verify: 3
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 172.16.1.5, remote crypto endpt.: 172.16.1.2
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet2/0
current outbound spi: 0x2BA4CAE8(732220136)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x90042D99(2416192921)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: 1, sibling_flags 80000040, crypto map: CRYPTO_MAP
sa timing: remaining key lifetime (k/sec): (4358826/2898)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x2BA4CAE8(732220136)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: 2, sibling_flags 80000040, crypto map: CRYPTO_MAP
sa timing: remaining key lifetime (k/sec): (4358826/2898)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
interface: FastEthernet3/0
Crypto map tag: CRYPTO_MAP, local addr 172.16.1.5
protected vrf: (none)
local ident (addr/mask/prot/port): (172.16.1.6/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (172.16.1.1/255.255.255.255/0/0)
current_peer 172.16.1.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 3, #pkts encrypt: 3, #pkts digest: 3
#pkts decaps: 3, #pkts decrypt: 3, #pkts verify: 3
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 172.16.1.5, remote crypto endpt.: 172.16.1.2
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet2/0
current outbound spi: 0x2BA4CAE8(732220136)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x90042D99(2416192921)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: 1, sibling_flags 80000040, crypto map: CRYPTO_MAP
sa timing: remaining key lifetime (k/sec): (4358826/2898)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x2BA4CAE8(732220136)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: 2, sibling_flags 80000040, crypto map: CRYPTO_MAP
sa timing: remaining key lifetime (k/sec): (4358826/2898)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
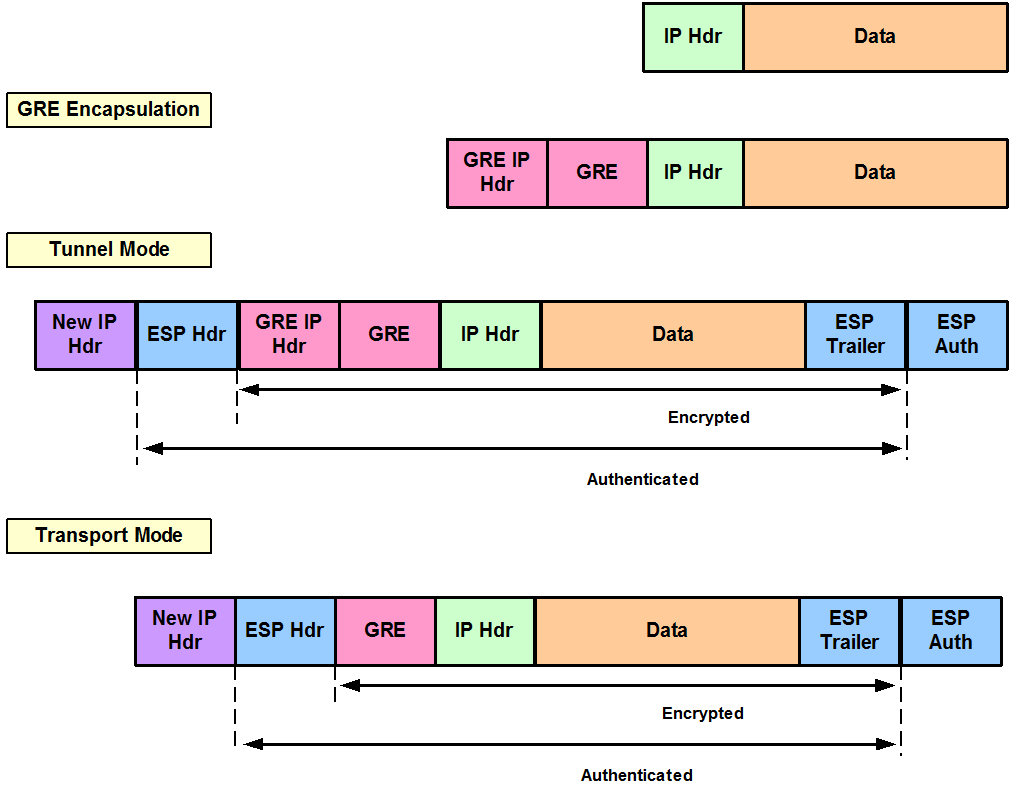
Figure 3 shows the two modes of ESP encapsulation: Transport mode and Tunnel mode. Tunnel Mode is used by default and encrypts the original IP packet and adds a new IP Header. On the other hand, Transport Mode encrypts the Data and uses the original IP Header saving 20 bytes (IP Header size) overhead.

Figure 3
In our particular topology, R2 happens to choose the path through R4 to route to R5. If we check the output of a capture done on R2’s Fa3/0 we can see the negotiation exchange to trigger the tunnel and the Ping echo and reply being encrypted.
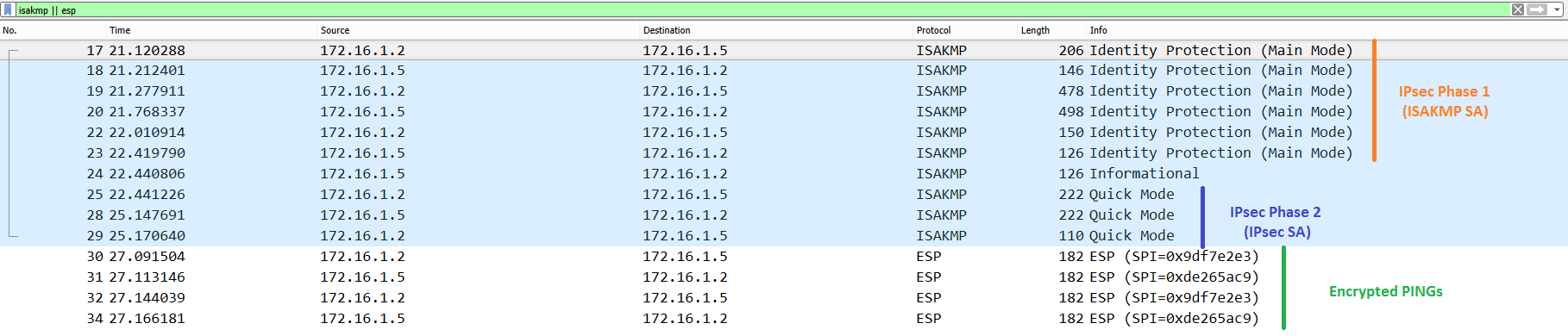
Figure 4
Now, we change the default Tunnel mode to Transport mode in the transform-set.
R2(cfg-crypto-trans)# mode transport
R5(cfg-crypto-trans)# mode transport
We check the IPsec SAs between the tunnel endpoints and we still see the encapsulation as Tunnel mode even having the encapsulation mode configured as Transport.
crypto ipsec transform-set ESP-3DES-MD5-HMAC esp-3des esp-md5-hmac
mode transport
R2#show crypto ipsec sa | inc Tunnel|Transport
in use settings ={Tunnel, }
in use settings ={Tunnel, }
in use settings ={Tunnel, }
in use settings ={Tunnel, }
crypto ipsec transform-set ESP-3DES-MD5-HMAC esp-3des esp-md5-hmac
mode transport
R5#show crypto ipsec sa | inc Tunnel|Transport
in use settings ={Tunnel, }
in use settings ={Tunnel, }
in use settings ={Tunnel, }
in use settings ={Tunnel, }
The reason is when Proxy ACLs include IP addresses beyond of the two peer endpoints (R2 and R5 in our scenario) the mode Transport setting is ignored, and Tunnel mode is negotiated. 172.16.1.1/32 (R1’s loopback) and 172.16.1.6/32 (R6’s loopback) are not our tunnel endpoints; they define the interesting traffic we want to encrypt through the tunnel. We will see how this applies to other examples later on.
GRE over IPsec with Crypto Maps
GRE encapsulation allows having an interface Tunnel which can be used for dynamic routing. This is a big advantage over Crypto Maps.
GRE over IPsec means that we do GRE first and encryption second. This simplifies the Proxy ACL that only needs to match GRE traffic between the tunnel endpoints. All traffic going through the tunnel is implicitly being encrypted.
Crypto Maps are applied to the physical interfaces, not the Tunnel interface. If we would apply the Crypto Map to the tunnel we would do encryption first and GRE second, which translates into a Proxy ACL that needs to match end to end traffic flows. This over complicates the design.
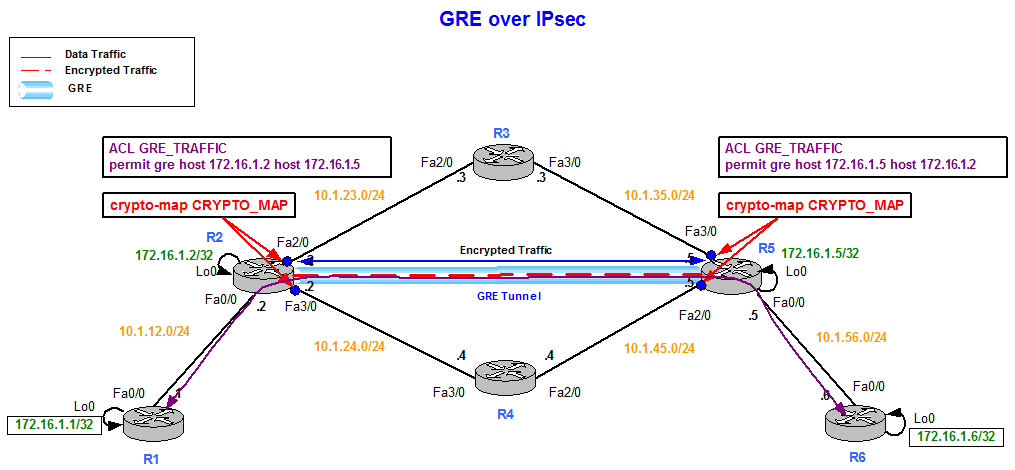
Figure 5
R2:
permit gre host 172.16.1.2 host 172.16.1.5
crypto isakmp policy 10
hash md5
authentication pre-share
group 14
crypto isakmp key CRYPTO_PASSWORD address 172.16.1.5
crypto ipsec transform-set ESP-3DES-MD5-HMAC esp-3des esp-md5-hmac
mode tunnel
crypto map CRYPTO_MAP local-address Loopback0
crypto map CRYPTO_MAP 10 ipsec-isakmp
set peer 172.16.1.5
set transform-set ESP-3DES-MD5-HMAC
match address GRE_TRAFFIC
interface FastEthernet2/0
ip address 10.1.23.2 255.255.255.0
crypto map CRYPTO_MAP
interface FastEthernet3/0
ip address 10.1.24.2 255.255.255.0
crypto map CRYPTO_MAP
interface Tunnel25
ip address 25.25.25.2 255.255.255.0
tunnel source Loopback0
tunnel destination 172.16.1.5
R5:
permit gre host 172.16.1.5 host 172.16.1.2
crypto isakmp policy 10
hash md5
authentication pre-share
group 14
crypto isakmp key CRYPTO_PASSWORD address 172.16.1.2
crypto ipsec transform-set ESP-3DES-MD5-HMAC esp-3des esp-md5-hmac
mode tunnel
crypto map CRYPTO_MAP local-address Loopback0
crypto map CRYPTO_MAP 10 ipsec-isakmp
set peer 172.16.1.2
set transform-set ESP-3DES-MD5-HMAC
match address GRE_TRAFFIC
interface FastEthernet2/0
ip address 10.1.45.5 255.255.255.0
crypto map CRYPTO_MAP
interface FastEthernet3/0
ip address 10.1.35.5 255.255.255.0
crypto map CRYPTO_MAP
interface Tunnel25
ip address 25.25.25.5 255.255.255.0
tunnel source Loopback0
tunnel destination 172.16.1.2
R2:
R2# show crypto ipsec sa | inc interface|local ident|remote ident|in use settings
interface: FastEthernet2/0
local ident (addr/mask/prot/port): (172.16.1.2/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (172.16.1.5/255.255.255.255/47/0)
in use settings ={Tunnel, }
in use settings ={Tunnel, }
interface: FastEthernet3/0
local ident (addr/mask/prot/port): (172.16.1.2/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (172.16.1.5/255.255.255.255/47/0)
in use settings ={Tunnel, }
in use settings ={Tunnel, }
R5:
interface: FastEthernet2/0
local ident (addr/mask/prot/port): (172.16.1.5/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (172.16.1.2/255.255.255.255/47/0)
in use settings ={Tunnel, }
in use settings ={Tunnel, }
interface: FastEthernet3/0
local ident (addr/mask/prot/port): (172.16.1.2/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (172.16.1.5/255.255.255.255/47/0)
in use settings ={Tunnel, }
in use settings ={Tunnel, }
As I mentioned before, IPsec in Tunnel mode is the default option. The establishment of the GRE tunnel between R2 and R5 is what triggers the ESP tunnel establishment. The Proxy ACL is not matching the final traffic flow anymore (ping from R1’s Loopback0 to R6’s Loopback0).
If we run a ping between R1’s loopback and R6’s loopback we can see that we do not lose any packets this time because the ESP tunnel has been already established (GRE tunnel is up).
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.6, timeout is 2 seconds:
Packet sent with a source address of 172.16.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 52/62/96 ms
Figure 6 shows the encapsulation of GRE over IPsec in Tunnel and Transport Mode. GRE adds a new IP Header (GRE IP Hdr) which means if we run IPsec in Tunnel mode we have 3 IP Headers (New IP Hdr and GRE IP Hdr are equal) versus the 2 IP Headers of running IPsec in Transport Mode. Transport mode does not use the GRE IP Hdr which saves 20 bytes overhead (This is the preferred encapsulation mode for GRE over IPsec).

Figure 6
We remove the Crypto Map configuration from R2’s and R5’s interfaces for a moment and we run a Ping from R1’s Loopback0 to R6’s Loopback0.
R2(config-if)#no crypto map CRYPTO_MAP
R2(config)#interface FastEthernet3/0
R2(config-if)#no crypto map CRYPTO_MAP
R5(config-if)#no crypto map CRYPTO_MAP
R5(config)#interface FastEthernet3/0
R5(config-if)#no crypto map CRYPTO_MAP
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.6, timeout is 2 seconds:
Packet sent with a source address of 172.16.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 52/62/96 ms
Figure 7 shows the Pings on a capture run on R2’s Fa3/0. The L2 Ethernet frame size without any IPsec configuration and only the GRE Encapsulation is 138 bytes: 138 – (14 (Ethernet Hdr) + 20 (GRE IP Hdr) + 4 (GRE) + 20 (IP Hdr)) = 80 bytes (Ping data – payload).
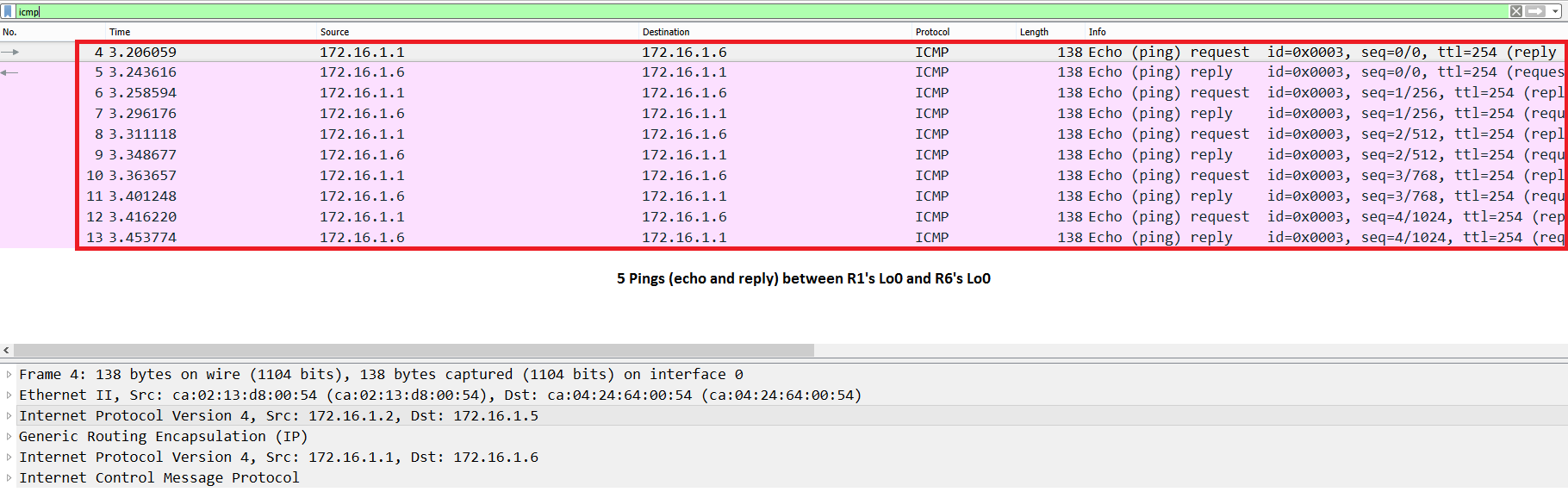
Figure 7
Now we reapply the Crypto Maps on R2 and R5’s interfaces and we do the same Ping.
R2(config-if)#crypto map CRYPTO_MAP
R2(config)#interface FastEthernet3/0
R2(config-if)#crypto map CRYPTO_MAP
R5(config-if)#crypto map CRYPTO_MAP
R5(config)#interface FastEthernet3/0
R5(config-if)# crypto map CRYPTO_MAP
Figure 8 shows the Pings between R1’s Loopback0 and R6’s Loopback0 on a capture run on R2’s Fa3/0. The packet size is 190 bytes in Tunnel Mode: 190 – (14 (Ethernet Hdr) +20 (New IP Hdr)) = 156 bytes (encrypted payload).
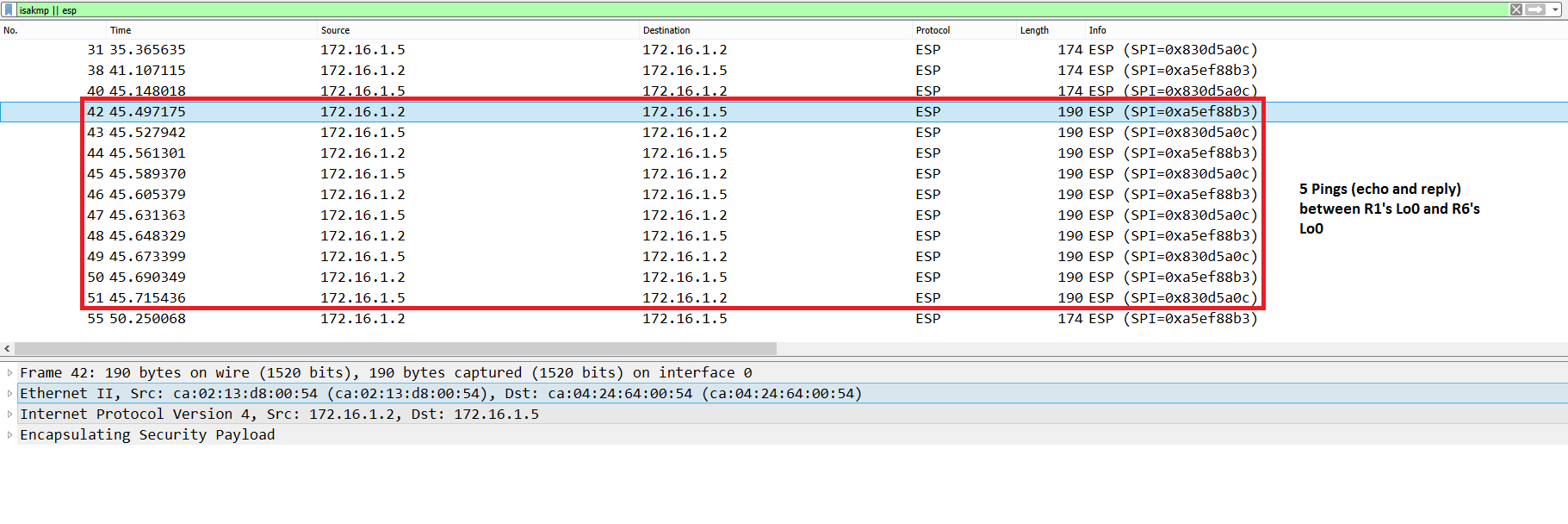
Figure 8
We now change the ESP Mode to Transport.
R2(cfg-crypto-trans)# mode transport
R5(cfg-crypto-trans)# mode transport
We flap the interfaces where the Crypto Maps have been applied and we clear the ISAKMP and IPsec SAs.
R2:
R2(config-if)#shut
R2(config)#interface fa3/0
R2(config-if)#shut
R2#clear crypto isakmp
R2#clear crypto sa
R2(config)#interface fa2/0
R2(config-if)#no shut
R2(config)#int fa3/0
R2(config-if)#no shut
R5:
R5(config-if)#shut
R5(config)#interface Fa3/0
R5(config-if)#shut
R5#clear crypto isakmp
R5#clear crypto sa
R5(config)#interface Fa2/0
R5(config-if)#no shut
R5(config)#interface Fa3/0
R5(config-if)#no shut
This time we can see the change to Transport Mode actually worked. This is because the Proxy ACL matches the tunnel endpoints, 172.16.1.2 (R2’s Lo0) and 172.16.1.5 (R5’s Lo0).
R2# show crypto ipsec sa | inc interface|local ident|remote ident|in use settings
interface: FastEthernet2/0
local ident (addr/mask/prot/port): (172.16.1.2/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (172.16.1.5/255.255.255.255/47/0)
in use settings ={Transport, }
in use settings ={Transport, }
in use settings ={Transport, }
in use settings ={Transport, }
interface: FastEthernet3/0
local ident (addr/mask/prot/port): (172.16.1.2/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (172.16.1.5/255.255.255.255/47/0)
in use settings ={Transport, }
in use settings ={Transport, }
in use settings ={Transport, }
in use settings ={Transport, }
R5# show crypto ipsec sa | inc interface|local ident|remote ident|in use settings
interface: FastEthernet2/0
local ident (addr/mask/prot/port): (172.16.1.5/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (172.16.1.2/255.255.255.255/47/0)
in use settings ={Transport, }
in use settings ={Transport, }
in use settings ={Transport, }
in use settings ={Transport, }
interface: FastEthernet3/0
local ident (addr/mask/prot/port): (172.16.1.5/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (172.16.1.2/255.255.255.255/47/0)
in use settings ={Transport, }
in use settings ={Transport, }
in use settings ={Transport, }
in use settings ={Transport, }
The output of a capture run on R2’s Fa3/0 interface shows that the packet size is now 174 bytes: 174 – (14 (Ethernet Hdr) + 20 (New IP Hdr)) = 140 bytes (encrypted payload). This means the encrypted payload is now 140 bytes versus the 156 bytes of ESP Tunnel mode. This is because we are not using the GRE IP Hdr (20 bytes) in Transport Mode anymore.
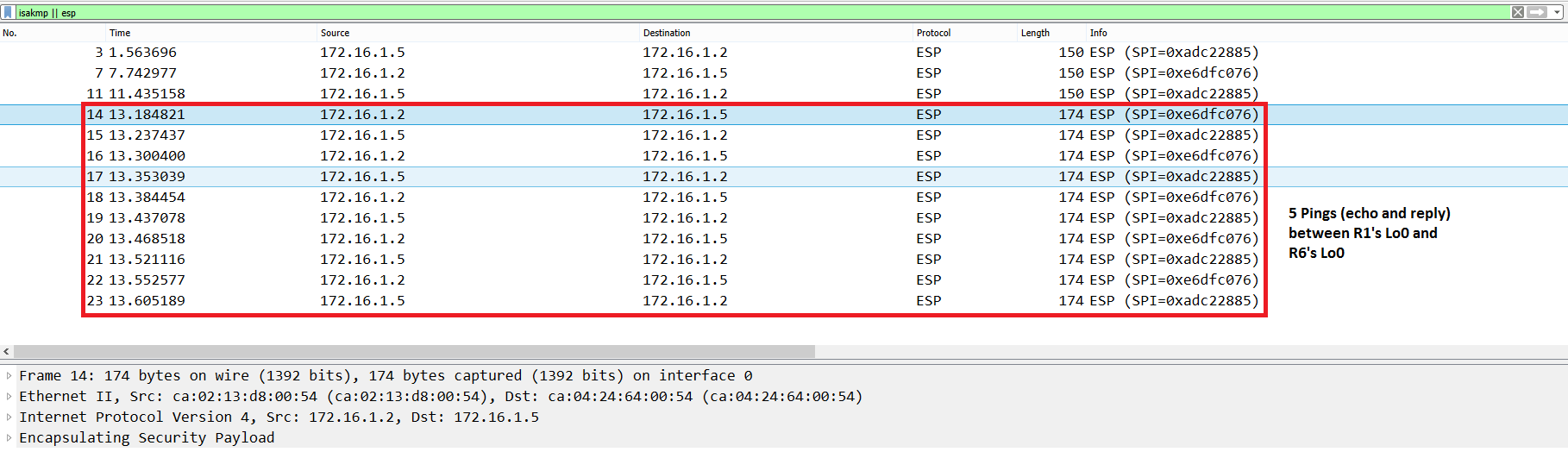
Figure 9
The result is not exactly 20 bytes difference between Tunnel and Transport modes in the Ping output. This is because the final encrypted packet size depends on the payload size, encryption method and the block size used which do not always result in the same length.
Fragmentation
An important thing to consider is fragmentation issues with Crypto Maps. The “Don’t Fragment” (DF) bit from the original IP Header is copied to GRE but it is not copied to ESP. Therefore, Path Maximum Transmission Unit (MTU) Discovery is broken and the MTU cannot be automatically discovered. This means fragmentation is going to happen when the IP packet is larger than the default MTU of 1500 bytes.
Assuming our tunnel is running in Tunnel mode, we ping to R6’s Lo0 from R1’s Lo0 with the DF bit set and a payload size of 1436 bytes: 1500 (default IP MTU) – ((20 New IP Hdr) + ? (ESP Hdr) + 20 (IP GRE Hdr) + 4 (GRE) + 20 (Original IP Hdr)) = 1436 bytes. 1436 bytes would be the maximum ping payload without counting the bytes for ESP encapsulation. We know this packet requires fragmentation as we have not taken ESP encapsulation into account. However, the ping is sent and fragmentation is happening in the background (MTU discovery is broken).
Type escape sequence to abort.
Sending 5, 1436-byte ICMP Echos to 172.16.1.6, timeout is 2 seconds:
Packet sent with a source address of 172.16.1.1
Packet sent with the DF bit set
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 40/40/44 ms
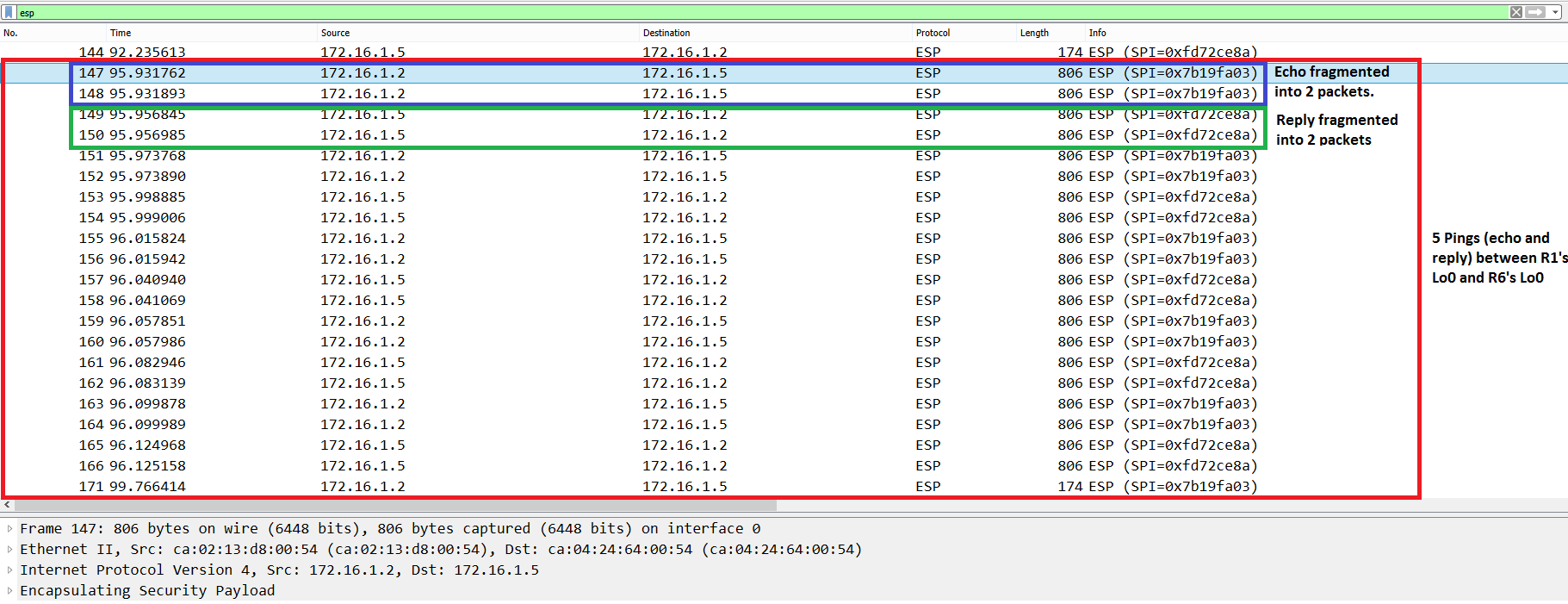
Figure 10
Now we try with a Ping of 1423 bytes length but it is still fragmented.
Type escape sequence to abort.
Sending 5, 1436-byte ICMP Echos to 172.16.1.6, timeout is 2 seconds:
Packet sent with a source address of 172.16.1.1
Packet sent with the DF bit set
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 40/40/44 ms
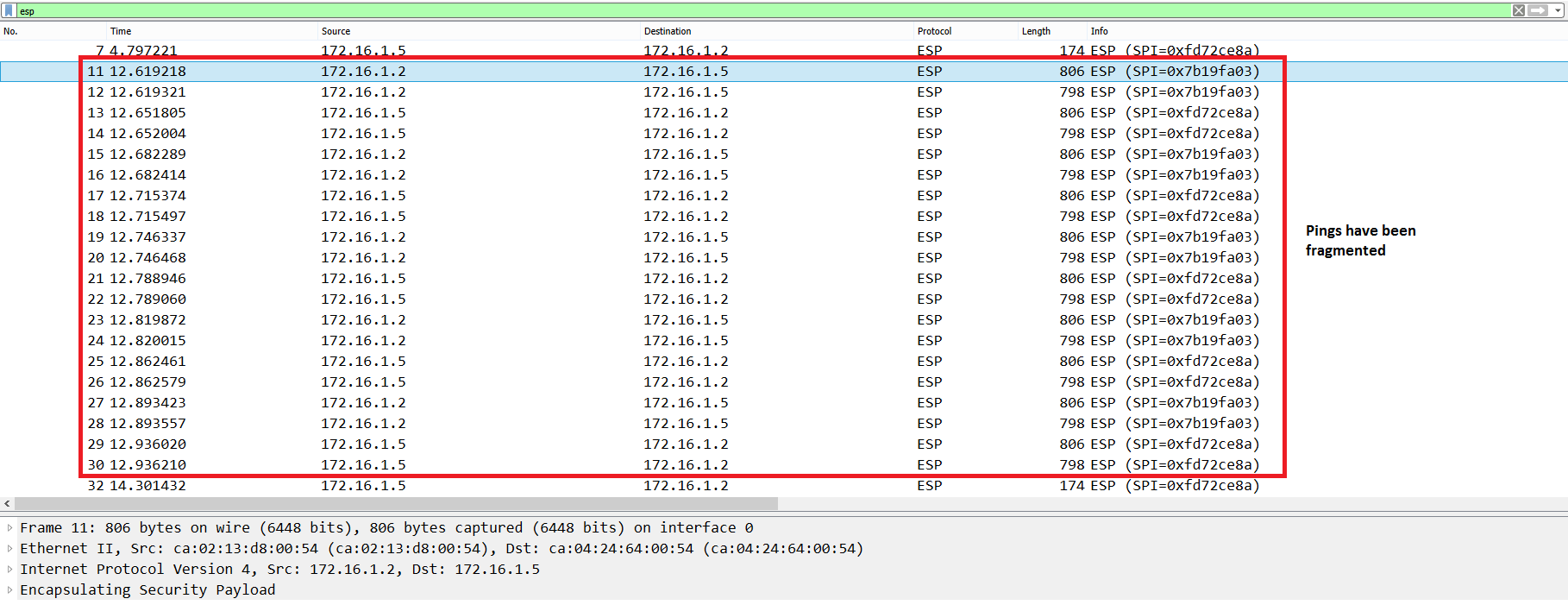
Figure 11
We try again with a Ping of 1422 bytes length. The output of the capture in Figure 12 shows that Pings have not been fragmented this time. Therefore, this is our maximum payload size for the default 1500 bytes MTU that does not require fragmentation.
Type escape sequence to abort.
Sending 5, 1436-byte ICMP Echos to 172.16.1.6, timeout is 2 seconds:
Packet sent with a source address of 172.16.1.1
Packet sent with the DF bit set
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 40/40/44 ms
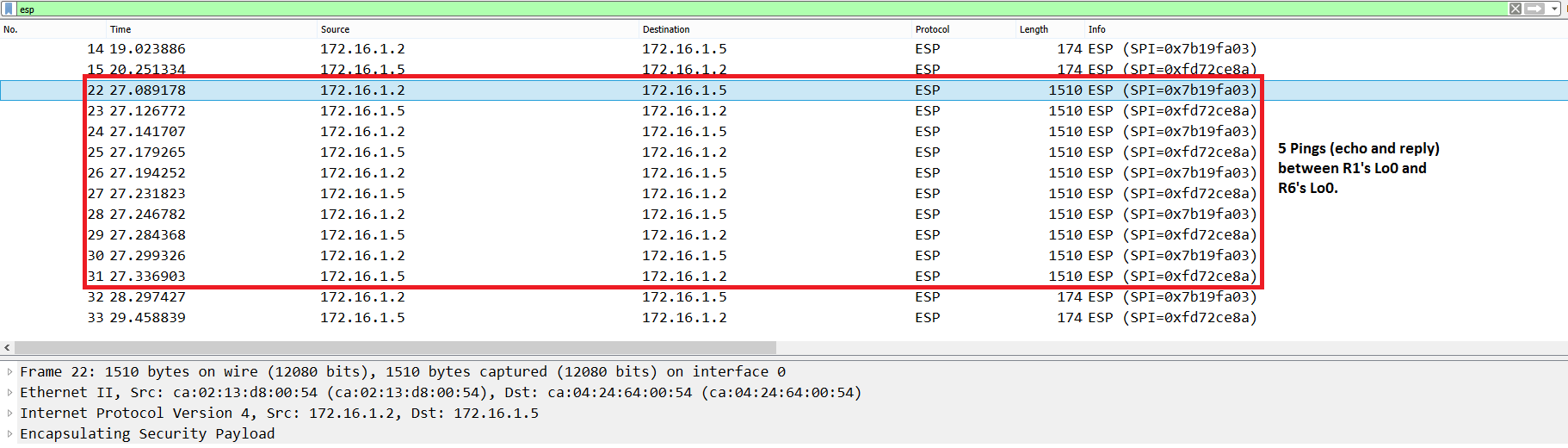
Figure 12
We manually configure the IP MTU to our maximum payload size, 1422 bytes, on the Tunnel interface.
R2(config-if)#ip mtu 1422
R2(config-if)#do show ip interface tunnel25
Tunnel25 is up, line protocol is up
Internet address is 25.25.25.2/24
Broadcast address is 255.255.255.255
Address determined by non-volatile memory
MTU is 1422 bytes
[…]
R5(config-if)#ip mtu 1422
R5(config-if)#do show ip interface tunnel25
Tunnel25 is up, line protocol is up
Internet address is 25.25.25.5/24
Broadcast address is 255.255.255.255
Address determined by non-volatile memory
MTU is 1422 bytes
[…]
We ping to R6’s Loopback0 from R1’s Loopback0 with a size of 1423 bytes. Now we see that the M (Must Fragment) bit is returned and the Ping is not sent. If we run the same Ping with a payload size of 1422 bytes, this time the Ping is sent and fragmentation does not occur (Figure 13).
Type escape sequence to abort.
Sending 5, 1423-byte ICMP Echos to 172.16.1.6, timeout is 2 seconds:
Packet sent with a source address of 172.16.1.1
Packet sent with the DF bit set
MMMMM
Success rate is 0 percent (0/5)
Type escape sequence to abort.
Sending 5, 1422-byte ICMP Echos to 172.16.1.6, timeout is 2 seconds:
Packet sent with a source address of 172.16.1.1
Packet sent with the DF bit set
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 52/55/68 ms
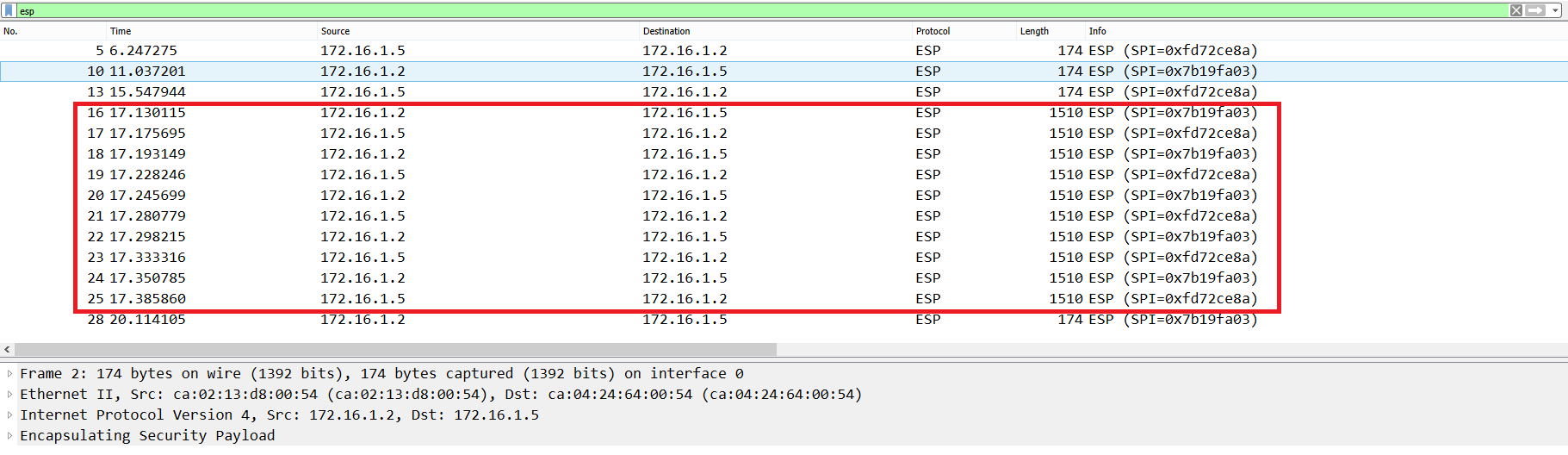
Figure 13
Therefore, it is recommended to use a MTU of 1400 bytes and a TCP Maximum Segment Size (MSS) of 1360 bytes (MTU – 40 bytes (20 bytes TCP Hdr + 20 bytes IP Hdr)) for GRE over IPsec using Crypto Maps. This way we avoid ESP packets being fragmented and they can still be hardware switching. Otherwise ESP packets might need fragmentation and the fragments will need to be software switching reducing the performance and throughput of the tunnel.
GRE over IPsec with IPsec Profile
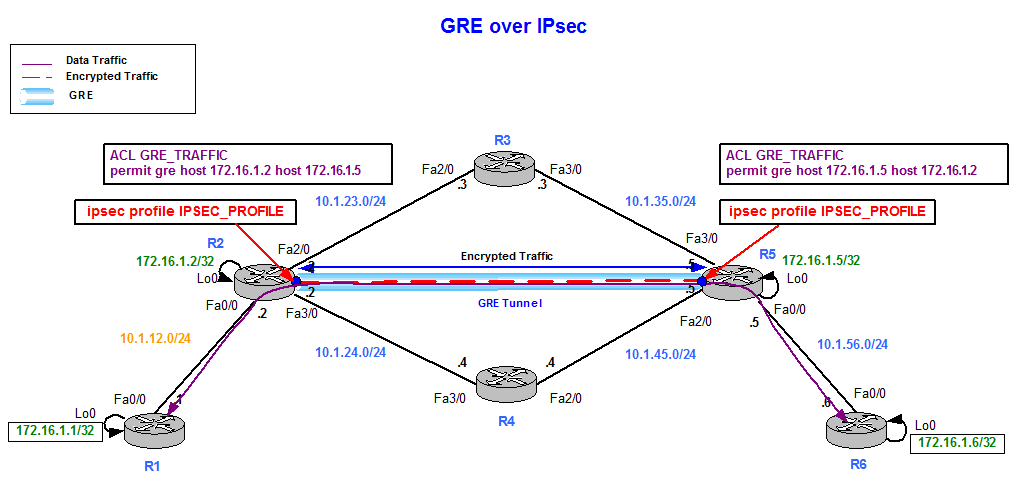
Figure 14
This configuration does not require a Crypto Map; instead a Crypto IPsec profile applied to the Tunnel interface is configured.
R2:
hash md5
authentication pre-share
group 14
crypto isakmp key CRYPTO_PASSWORD address 172.16.1.5
crypto ipsec transform-set ESP-3DES-MD5-HMAC esp-3des esp-md5-hmac
mode tunnel
crypto ipsec profile IPSEC_PROFILE
set transform-set ESP-3DES-MD5-HMAC
interface Tunnel25
tunnel protection ipsec profile IPSEC_PROFILE
R5:
hash md5
authentication pre-share
group 14
crypto isakmp key CRYPTO_PASSWORD address 172.16.1.2
crypto ipsec transform-set ESP-3DES-MD5-HMAC esp-3des esp-md5-hmac
mode tunnel
crypto ipsec profile IPSEC_PROFILE
set transform-set ESP-3DES-MD5-HMAC
interface Tunnel25
tunnel protection ipsec profile IPSEC_PROFILE
IPsec Phase 1 and Phase 2 are successfully completed. Note that the only difference is the IPsec SA is formed through the tunnel and not through the physical interfaces anymore. It also generates the PROXY ACL automatically (it gets the peering information from the Tunnel interface).
R2:
IPv4 Crypto ISAKMP SA
dst src state conn-id status
172.16.1.5 172.16.1.2 QM_IDLE 1004 ACTIVE
172.16.1.2 172.16.1.5 QM_IDLE 1003 ACTIVE
R2# show crypto ipsec sa | inc interface|local ident|remote ident|in use settings
interface: Tunnel25
local ident (addr/mask/prot/port): (172.16.1.2/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (172.16.1.5/255.255.255.255/47/0)
in use settings ={Tunnel, }
in use settings ={Tunnel, }
in use settings ={Tunnel, }
in use settings ={Tunnel, }
R5:
IPv4 Crypto ISAKMP SA
dst src state conn-id status
172.16.1.2 172.16.1.5 QM_IDLE 1003 ACTIVE
172.16.1.5 172.16.1.2 QM_IDLE 1004 ACTIVE
R5# show crypto ipsec sa | inc interface|local ident|remote ident|in use settings
interface: Tunnel25
local ident (addr/mask/prot/port): (172.16.1.5/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (172.16.1.2/255.255.255.255/47/0)
in use settings ={Tunnel, }
in use settings ={Tunnel, }
in use settings ={Tunnel, }
in use settings ={Tunnel, }
We run the same Ping between R1 and R6’s Loopbacks. The output shows the default Ping size is 190 bytes running in Tunnel Mode. Nothing has changed with respect to the previous configuration (GRE over IPsec with Crypto Maps).
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.6, timeout is 2 seconds:
Packet sent with a source address of 172.16.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 72/84/112 ms
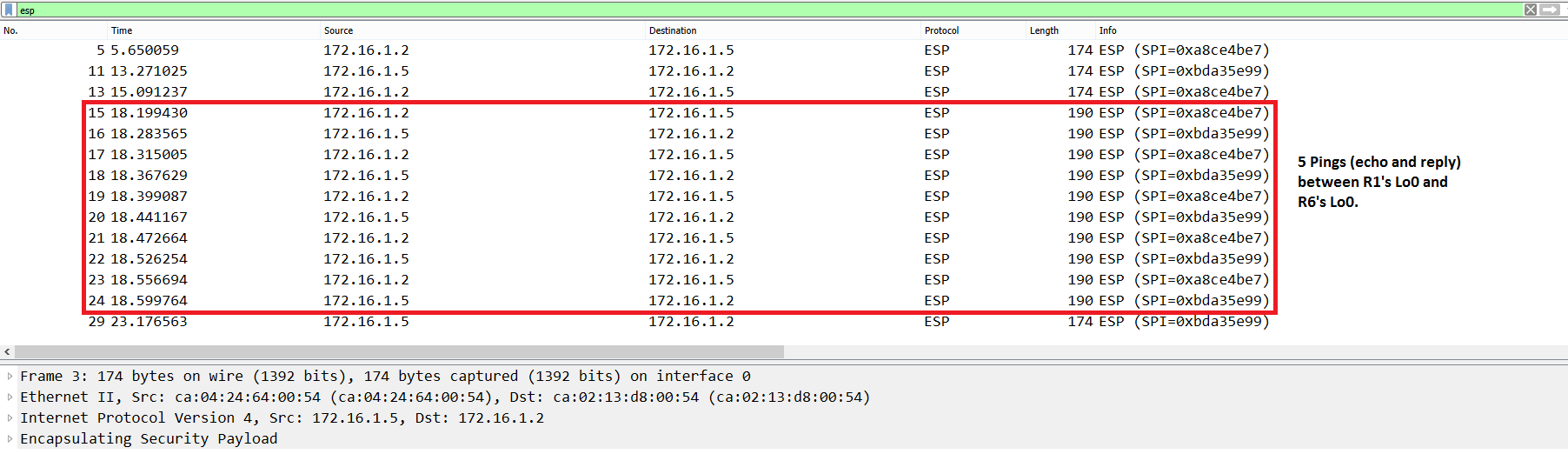
Figure 15
Fragmentation
Using IPsec Profiles, the DF bit is copied to the ESP header. The router is going to find out the MTU, we do not have to manually configure it with the command “ip mtu x”. When the routers do the negotiation they agree on the MTU based on the configuration of the transform set.
The result of the ping with a larger payload size than the MTU negotiated returns the M bit.
Type escape sequence to abort.
Sending 5, 1423-byte ICMP Echos to 172.16.1.6, timeout is 2 seconds:
Packet sent with a source address of 172.16.1.1
Packet sent with the DF bit set
MMMMM
Success rate is 0 percent (0/5)
Type escape sequence to abort.
Sending 5, 1422-byte ICMP Echos to 172.16.1.6, timeout is 2 seconds:
Packet sent with a source address of 172.16.1.1
Packet sent with the DF bit set
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 60/63/68 ms
Fragmentation does not occur with IPsec profiles. However we might still want to enforce TCP MSS to 40 bytes lower than the MTU value.
Tunnel25 is up, line protocol is up
Hardware is Tunnel
Internet address is 25.25.25.2/24
MTU 17862 bytes, BW 100 Kbit/sec, DLY 50000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation TUNNEL, loopback not set
Keepalive not set
Tunnel source 172.16.1.2 (Loopback0), destination 172.16.1.5
Tunnel Subblocks:
src-track:
Tunnel25 source tracking subblock associated with Loopback0
Set of tunnels with source Loopback0, 1 member (includes iterators), on interface <OK>
Tunnel protocol/transport GRE/IP
Key disabled, sequencing disabled
Checksumming of packets disabled
Tunnel TTL 255, Fast tunneling enabled
Tunnel transport MTU 1422 bytes
Tunnel transmit bandwidth 8000 (kbps)
Tunnel receive bandwidth 8000 (kbps)
Tunnel protection via IPSec (profile “IPSEC_PROFILE”)
Last input 00:00:07, output 00:23:11, output hang never
R2(config-if)#ip tcp adjust-mss 1382
R5(config-if)#ip tcp adjust-mss 1382
Virtual Tunnel Interface
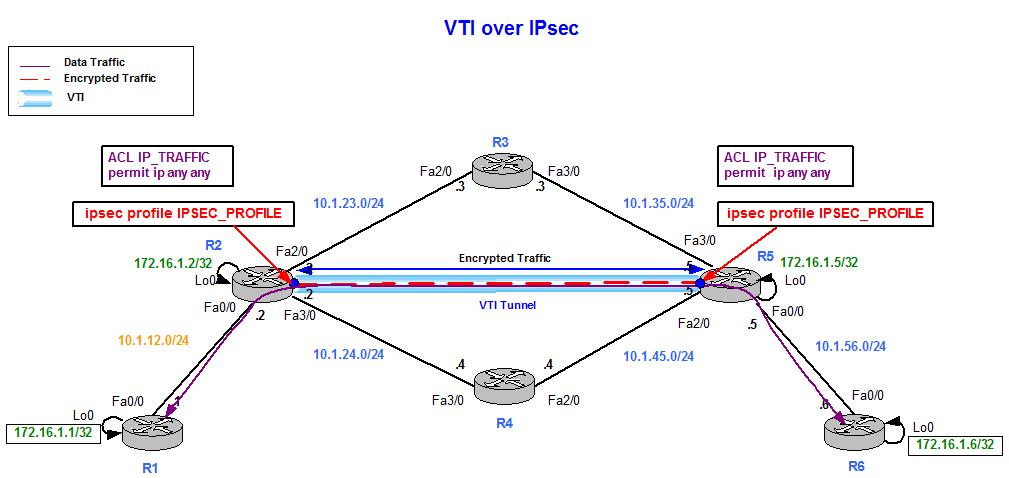
Figure 16
VTI site to site is directly encapsulated over IPsec. It does not require GRE encapsulation, which reduces overhead. However, VTI only allows IPv4 over IPv4 IPsec and IPv6 over IPv6 IPsec. In addition, VTI is always on so interesting traffic is not required for the tunnel to go up.
A key difference is the tunnel is up (line protocol is up) as long as IPsec Phase 2 is successfully completed. However, GRE over IPsec maintains the line protocol of the tunnel up if recursion to the next hop is successful. This does not actually ensure that we have end to end reachability to the destination.
R2:
hash md5
authentication pre-share
group 14
crypto isakmp key CRYPTO_PASSWORD address 172.16.1.5
crypto ipsec transform-set ESP-3DES-MD5-HMAC esp-3des esp-md5-hmac
mode tunnel
crypto ipsec profile IPSEC_PROFILE
set transform-set ESP-3DES-MD5-HMAC
interface Tunnel25
tunnel mode ipsec ipv4
tunnel protection ipsec profile IPSEC_PROFILE
R5:
crypto isakmp policy 10
hash md5
authentication pre-share
group 14
crypto isakmp key CRYPTO_PASSWORD address 172.16.1.2
crypto ipsec transform-set ESP-3DES-MD5-HMAC esp-3des esp-md5-hmac
mode tunnel
crypto ipsec profile IPSEC_PROFILE
set transform-set ESP-3DES-MD5-HMAC
interface Tunnel25
tunnel mode ipsec ipv4
tunnel protection ipsec profile IPSEC_PROFILE
The output below shows IPsec Phase 1 and Phase 2 being successfully completed. A difference with GRE over IPsec is VTI defines any IP traffic as interesting traffic (Proxy ACL is not configurable). Any routing decision that makes the traffic goes through the tunnel implies the traffic will be encrypted.
R2:
IPv4 Crypto ISAKMP SA
dst src state conn-id status
172.16.1.5 172.16.1.2 QM_IDLE 1007 ACTIVE
172.16.1.2 172.16.1.5 QM_IDLE 1008 ACTIVE
R2# show crypto ipsec sa | inc interface|local ident|remote ident|in use settingsinterface: Tunnel25
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
in use settings ={Tunnel, }
in use settings ={Tunnel, }
in use settings ={Tunnel, }
in use settings ={Tunnel, }
R2#show interface tunnel25
Tunnel25 is up, line protocol is up
Hardware is Tunnel
Internet address is 25.25.25.2/24
MTU 17886 bytes, BW 100 Kbit/sec, DLY 50000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation TUNNEL, loopback not set
Keepalive not set
Tunnel source 172.16.1.2 (Loopback0), destination 172.16.1.5
Tunnel Subblocks:
src-track:
Tunnel25 source tracking subblock associated with Loopback0
Set of tunnels with source Loopback0, 1 member (includes iterators), on interface <OK>
Tunnel protocol/transport IPSEC/IP
Tunnel TTL 255
Tunnel transport MTU 1446 bytes
Tunnel transmit bandwidth 8000 (kbps)
Tunnel receive bandwidth 8000 (kbps)
Tunnel protection via IPSec (profile “IPSEC_PROFILE“)
[…]
R5:
IPv4 Crypto ISAKMP SA
dst src state conn-id status
172.16.1.2 172.16.1.5 QM_IDLE 1008 ACTIVE
172.16.1.5 172.16.1.2 QM_IDLE 1007 ACTIVE
R5# show crypto ipsec sa | inc interface|local ident|remote ident|in use settings
interface: Tunnel25
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
in use settings ={Tunnel, }
in use settings ={Tunnel, }
in use settings ={Tunnel, }
in use settings ={Tunnel, }
R5#show interface tunnel25
Tunnel25 is up, line protocol is up
Hardware is Tunnel
Internet address is 25.25.25.5/24
MTU 17886 bytes, BW 100 Kbit/sec, DLY 50000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation TUNNEL, loopback not set
Keepalive not set
Tunnel source 172.16.1.5 (Loopback0), destination 172.16.1.2
Tunnel Subblocks:
src-track:
Tunnel25 source tracking subblock associated with Loopback0
Set of tunnels with source Loopback0, 1 member (includes iterators), on interface <OK>
Tunnel protocol/transport IPSEC/IP
Tunnel TTL 255
Tunnel transport MTU 1446 bytes
Tunnel transmit bandwidth 8000 (kbps)
Tunnel receive bandwidth 8000 (kbps)
Tunnel protection via IPSec (profile “IPSEC_PROFILE“)
VTI only supports Tunnel mode because the Proxy ACL defines any IP traffic and does not specify traffic between the tunnel endpoints (requirement for Transport mode).
It is important to mention that most platforms cannot hardware accelerate GRE. So if ESP is supported in hardware, VTI is going to be faster than GRE.
We run the ping to R6’s Loopback0 from R1’s Loopback0 again and Figure 17 shows that is successfully encrypted. The size of the Ethernet frame is 166 bytes versus the 190 bytes of GRE in Tunnel mode. 190 bytes – (20 (GRE IP Hdr) + 4 (GRE)) = 166 bytes. We save 24 bytes overhead.
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.5, timeout is 2 seconds:
Packet sent with a source address of 172.16.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 32/32/32 ms
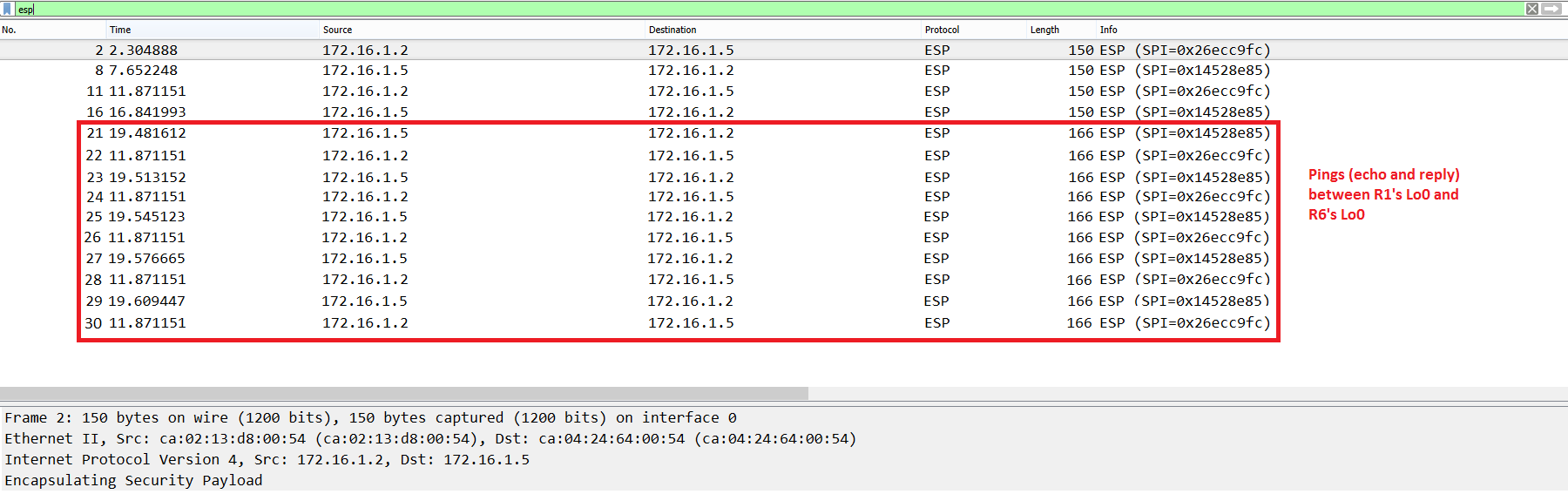
Figure 17
Fragmentation
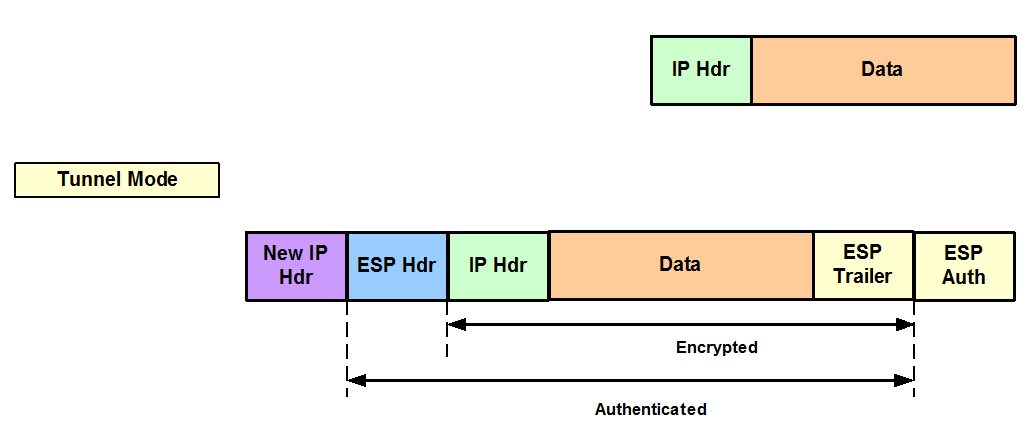
Figure 18
Because VTI uses an IPsec Profile we do not have issues with fragmentation. Path MTU can be discovered and only packets that meet the maximum MTU will be encrypted and forwarded.
Type escape sequence to abort.
Sending 5, 1423-byte ICMP Echos to 172.16.1.6, timeout is 2 seconds:
Packet sent with a source address of 172.16.1.1
Packet sent with the DF bit set
MMMMM
Success rate is 0 percent (0/5)
Type escape sequence to abort.
Sending 5, 1422-byte ICMP Echos to 172.16.1.6, timeout is 2 seconds:
Packet sent with a source address of 172.16.1.1
Packet sent with the DF bit set
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 60/63/68 ms
Configuration Summary
|
R2 |
R5 |
|
| ISAKMP Policy | crypto isakmp policy 10 hash md5 authentication pre-share group 14
crypto isakmp key CRYPTO_PASSWORD address 172.16.1.5 |
crypto isakmp policy 10 hash md5 authentication pre-share group 14
crypto isakmp key CRYPTO_PASSWORD address 172.16.1.2 |
| IPsec Transform set | crypto ipsec transform-set ESP-3DES-MD5-HMAC esp-3des esp-md5-hmac mode tunnel |
crypto ipsec transform-set ESP-3DES-MD5-HMAC esp-3des esp-md5-hmac mode tunnel |
| Crypto Maps | ip access-list extended IPSEC_TRAFFIC permit ip host 172.16.1.1 host 172.16.1.6
crypto map CRYPTO_MAP local-address Loopback0 interface FastEthernet2/0 interface FastEthernet3/0 |
ip access-list extended IPSEC_TRAFFIC permit ip host 172.16.1.6 host 172.16.1.1
crypto map CRYPTO_MAP local-address Loopback0 interface FastEthernet2/0 interface FastEthernet3/0 |
| GRE over IPsec with Crypto Maps | ip access-list extended GRE_TRAFFIC permit gre host 172.16.1.2 host 172.16.1.5
crypto map CRYPTO_MAP local-address Loopback0 interface FastEthernet2/0 interface FastEthernet3/0 |
ip access-list extended GRE_TRAFFIC permit gre host 172.16.1.5 host 172.16.1.2
crypto map CRYPTO_MAP local-address Loopback0 interface FastEthernet2/0 interface FastEthernet3/0 |
| GRE over IPsec with IPsec Profile | crypto ipsec profile IPSEC_PROFILE set transform-set ESP-3DES-MD5-HMAC
interface Tunnel25 |
crypto ipsec profile IPSEC_PROFILE set transform-set ESP-3DES-MD5-HMAC
interface Tunnel25 |
| VTI with Crypto Maps | crypto ipsec profile IPSEC_PROFILE set transform-set ESP-3DES-MD5-HMAC
interface Tunnel25 |
crypto ipsec profile IPSEC_PROFILE set transform-set ESP-3DES-MD5-HMAC
interface Tunnel25 |