This post describes different deployment scenarios where Network Address Translation (NAT) is implemented with IPsec DMVPN.
(more…)All posts tagged: security
bla, bla, bla .... :)
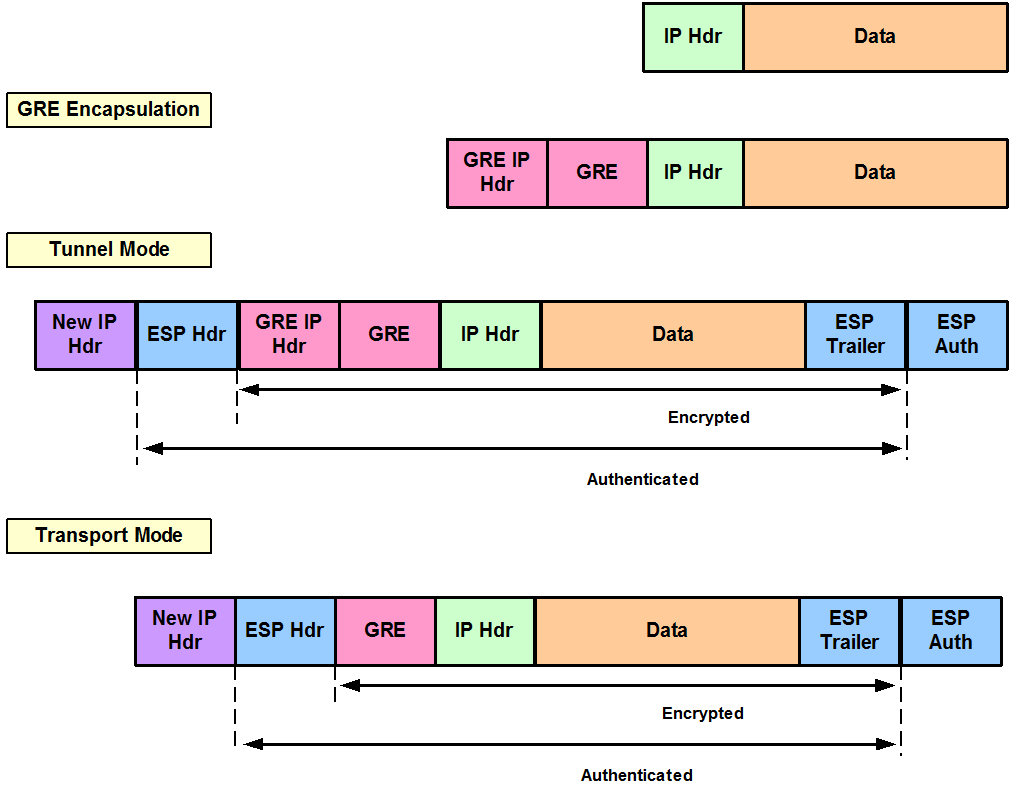
IPsec: Crypto Maps, GRE and VTI
This post describes the configuration of IPsec using four different methods in order to achieve authentication and encryption. We will compare the configuration requirements as well as the overhead introduced by each method from the point of view of packet size.
(more…)
Software Defined Networks and Security
Software Defined Networking (SDN) is a network architecture that simplifies network management and enables innovation in communication networks. SDN decouples the control and data planes; the control plane is logically centralized and makes the decisions that the data plane implements: the network becomes “programmable”. This separation of the control and data planes in SDN opens security challenges, such as man-in-the middle attacks, denial of service (DoS) attacks, and saturation attacks.
(more…)
Setting up Remote Access VPN for Firepower Threat Defense
Remote Access VPN (RA VPN) is available in Firepower Threat Defense (FTD) 6.2.1 for 2100 Platforms. For all other Platforms it will be supported on version 6.2.2.
(more…)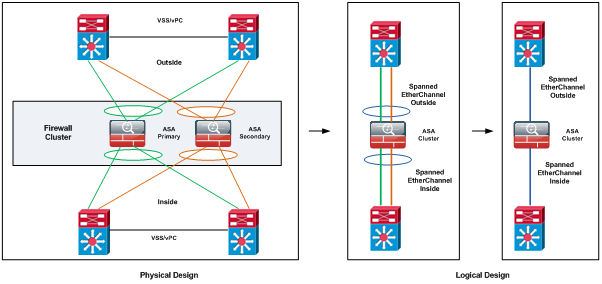
Cisco ASA Cluster – Spanned EtherChannel Mode
ASA clustering consists of multiple ASAs acting as a single unit, see Figure 1.
Spanned EtherChannel is the Cisco recommended implementation in which interfaces on multiple members of the cluster are grouped into a single EtherChannel; the EtherChannel performs load balancing between units.
(more…)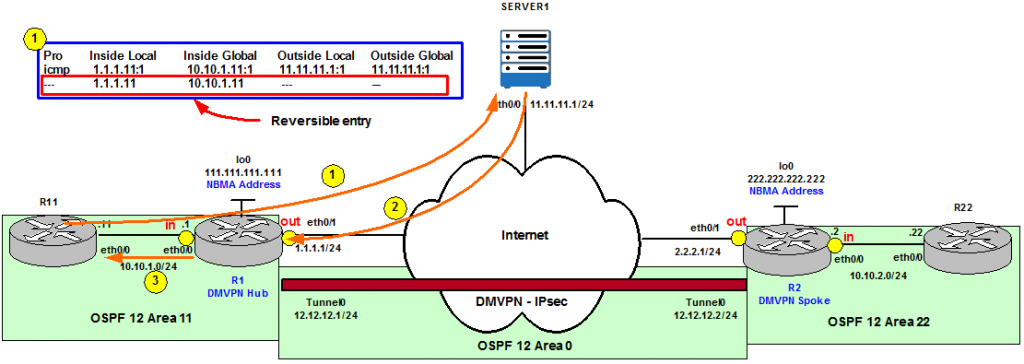
Recent Comments