Software Defined Networks and Security
Software Defined Networking (SDN) is a network architecture that simplifies network management and enables innovation in communication networks. SDN decouples the control and data planes; the control plane is logically centralized and makes the decisions that the data plane implements: the network becomes “programmable”. This separation of the control and data planes in SDN opens security challenges, such as man-in-the middle attacks, denial of service (DoS) attacks, and saturation attacks.
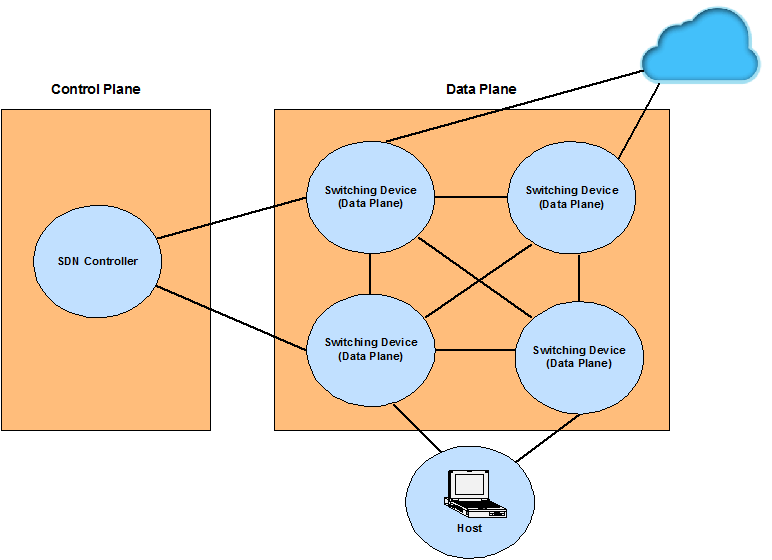
Figure 1
Security background
SDN architecture allows networks to monitor traffic and recognize threats to enforce security. The centralization of the control plane in a controller enables the distribution of security policies with no risk of policy collisions. These run-time decisions are able to update the security policies or add new security modules to the controller platform to face threats. The result can be rerouting or blocking traffic within a particular network area rather than changing the hardware or updating its firmware.
On the other hand, network security in legacy network architectures is considered as an overlay which relies on manually configurable perimeter-based solutions. The manual configuration of security systems such as firewalls, intrusion detection/prevention systems (IDS/IPS) and IPSec technologies are prone to errors and policy conflicts can happen which results in serious security breaches.
However, SDN has its own challenges and limitations in terms of security. Since a centralized controller is responsible for managing the entire network, the compromise of the controller can compromise the whole network. Therefore, securing the network from malicious applications or attacks is a key security challenge in SDN. Network security is the foundation of a successful network and communication between end devices must consequently be secured.
Security Challenges
Planes separation and centralized control plane functionality to a controller can be essential to the future of networking; however it also opens new security concerns. The control plane is more susceptible to attacks, especially DoS and DDoS attacks which can take the whole network down if the SDN controller is compromised. Communications between SND nodes must be secured and these resources must only be visible to legitimate applications.
Example of DoS Attack:
Generally a DoS attack targets multiple devices and tries, for example, to bring the CPU down to negatively impact the throughput and the service that one end device is providing.
In traditional networks, it happens on a per device basis and in most cases a DoS attack is isolated to a specific device.
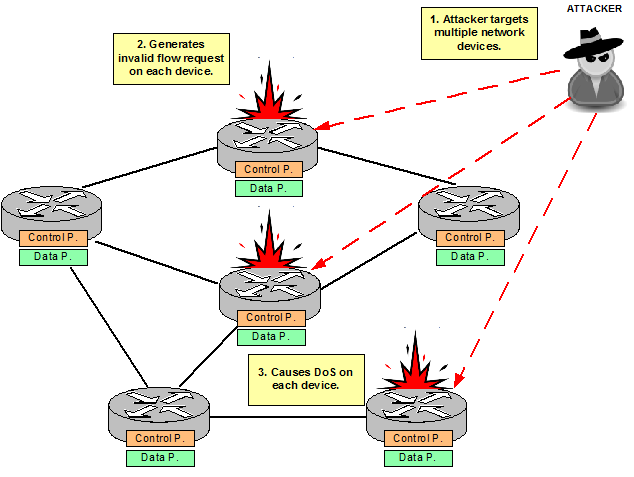
Figure 2
In a SDN network this behaviour changes; the attacker only needs to target one device (agent) in the network, perhaps injecting false flow information using the data plane, and that agent will then forward the changed flow information back to the controller. This flow can either make the controller’s CPU to go high or make the controller to push the invalid network flows to other agents impacting more than one SDN agent.
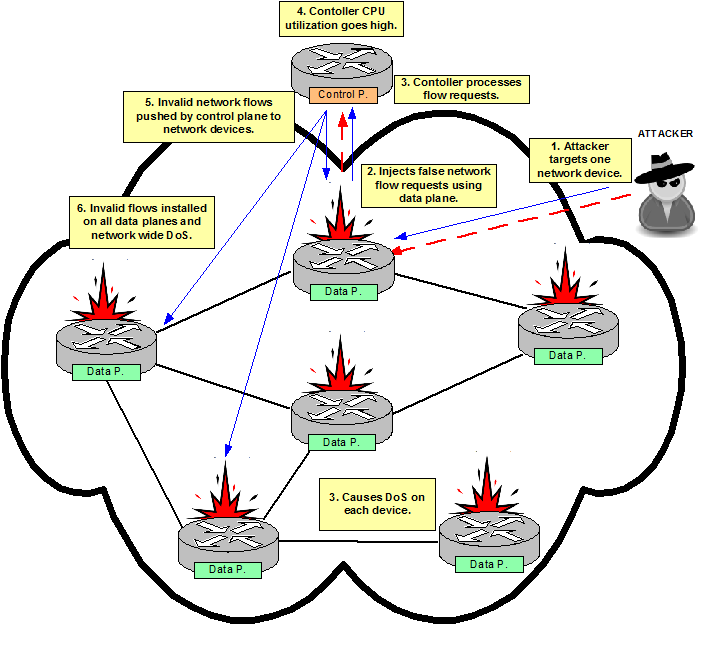
Figure 3
Security and SDN:
Security measures can be categorized in two types: Security for the SDN and Security by the SDN.
Security for the SDN
The SDN functionality itself must be protected as each layer in the implementation has its own perimeter. This is known as Security for the SDN.
It is important to keep in mind that the security tools and knowledge you have can play a significant role to deploy SDN in you network.
The following table covers some threats that you might face during SDN operation and some security measures that can help you to prevent any harm.
| SDN Component | SDN Sub-component | Threat | Security Measures |
| Controller Specific Hardening | Secure Access | Difficult to implement access control and accountability. No compelling mechanisms for enforcing access control. |
|
| Secure Operation | Lack of network visibility and security patch management. |
|
|
| Agent Services | Malicious or compromised devices can generate false flow rules which make difficult to check if an end device has been compromised. |
|
|
| Device Hardening (Agents and Controllers) | Control Plane | Centralizing intelligence in one entity will most likely have scalability and availability challenges.
Visible nature, centralized intelligence and limited resource of the control plane are the main reasons for attracting DoS attacks. |
|
| Management Plane | Difficult to implement access control and accountability. Lack of encryption and trust in default configurations. |
|
|
| Data Plane | Data plane is dumb and therefore more susceptible to fraudulent flow rules. |
|
|
| Network Services | Not having a complete picture of the network functionality and its critical services. |
|
|
| Applications and APIs | Getting tougher to manage security for your digital assets. Issues following best practices. |
|
|
| Management and Provisioning | No compelling mechanisms for enforcing access control. Tracking of Network Changes not in place. |
|
|
| Communication Channels | Lack of security for communications between SND nodes. Resources visible to illegitimate applications. |
|
Security by the SDN
Components of a SDN must provide a secure perimeter around services and access; this is known as Security by the SDN.
These are some security features that the SDN architecture provides:
- Security services integrated into agent systems such as:
- Identity management.
- Threat defense.
- Content Inspection.
- Security checks, configuration error checking, compliance and regulatory requirements can be built in and applied to policy, configurations, connections and flows.
- Attacks and anomalies are reported to controllers that can enforce network wide containment and distribute protection updates. This behaviour helps to limit and remove DoS impact on the network.
- Security is integrated in the deployment from day one. Security by the SDN is built as part of the architecture.
Summary
Security is one of the top concerns that need to be addressed when deploying SDN. SDN Architecture allows security to be integrated from day one and it is not considered as an overlay like in traditional networks. However, traditional security may not address the needs of SDN. This new architecture brings new vulnerabilities and might change the way common attacks impact on the network. Therefore, multiple layers of security are needed. Each component that shapes the SDN architecture must afford its own protection as well as additional security precautions can be taken to enforce and guarantee extra protection.
References